What to do if your mail server is targeted by phishing?
One of the users of my mail server entered their credentials into a phishing form sent via email. It was disguised as a commercial document and looked like this:
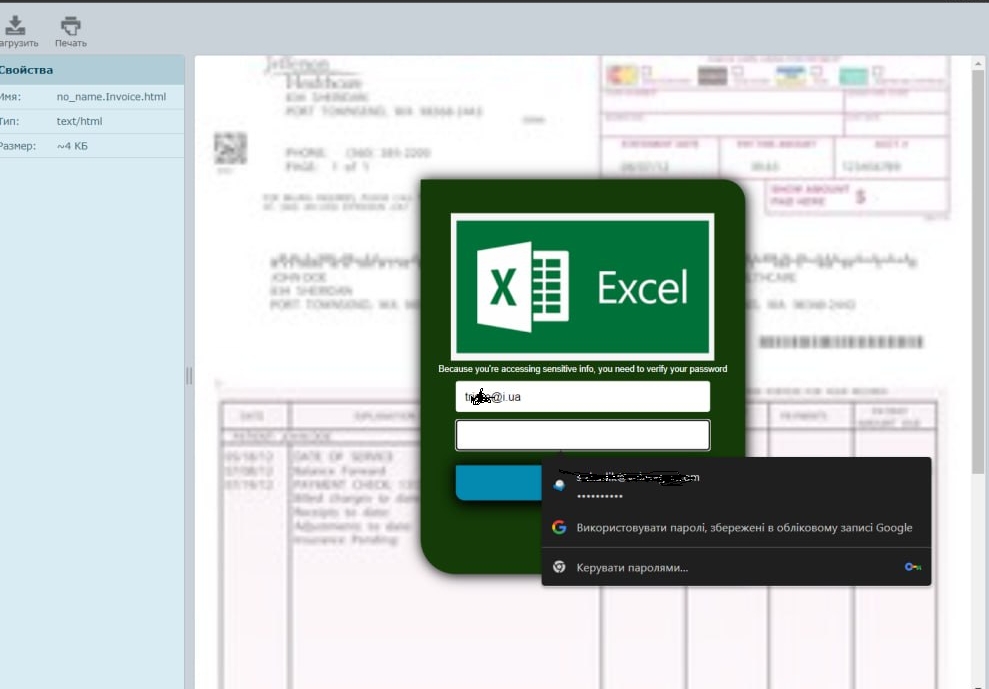
After that, for about a day (yes, it’s my oversight), my server was used to send out similar forms. Interestingly and amusingly, my colleague denies entering the data into the form – but they always do that (we know that everything breaks on its own, especially computer equipment and information systems) LMAO
So, first of all, I changed the password for the compromised user. He started receiving replies about nonexistent accounts from various servers – the variety of them shocked me. The attacker used an email address generator with mail lists, it seems to me.
About 30,000 responses came in within 3 days, and I also deleted the EXIM queue to send 40,000 messages with this command:
cd /var/spool/exim4/input #Mail queue directory exim -bp #Show messages ls -l | wc -l #Show quantity exiqgrep -i | xargs exim -Mrm #delete messages
I should consider security issues:
1) Limit the price of sending messages by time and quantity with account blocking and notification.
2) Password policies should be tightened.
3) Connect an antivirus gateway that would check emails before reaching the server to preliminarily exclude the delivery of phishing to my inexperienced users.
4) Conduct explanatory work among users.
